In-depth LoRaWAN
The information on this page is for those who want to delve deeper into LoRa technology. Start by reading What is LoRa.
The advantages of narrowband radio
High-frequency connections provide high data rates but have limited range at acceptable power levels (e.g. WiFi). For things with limited energy supply that need long range, low frequency operation is preferred. The lower the frequency, the less power is required to maintain a given link budget.
Lower frequency transmissions mean lower data rates, but IoT applications do not require large bandwidth. In addition, lower data rates provide another benefit in the form of reduced errors, reducing receiver sensitivity requirements. The disadvantage of slow communication is that it increases the transmission time, which increases the risk of interference from sound and other signals. In addition, longer transmission time means increased energy consumption at both the transmitter and receiver ends.
Narrowband radios can still meet the range, energy and data rate requirements required by most IoT applications. The modulation method in LoRa also reduces the disadvantages.
Modulation methods
For communication in the 868MHz band, spread spectrum modulation has previously been relied upon to reduce noise or interfering signals.
Although this can help at very high data rates, high bandwidth and sophisticated modulation signal chains are required for efficient transmission and reception of the broadband signal. IoT applications rarely need high data rates. The complexity and requirements associated with traditional spread spectrum technologies make them less effective for low-cost, battery-powered IoT. This is where LoRa comes in.
LoRa is a unique spread spectrum modulation method that provides some of the benefits of spread noise immunity while simplifying development requirements. LoRa modulation is based on a frequency modulated "chirp" signal.
When a LoRa transmission is initiated, a LoRa modem issues a preamble consisting of a series of chirps (see left image). The transmission continues with a series of chirps that encode data essentially as frequency jumps in the chirp signal (see right image).
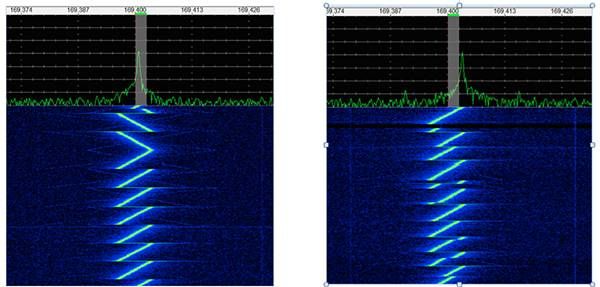
Image from Link labs
The receiving side can lock on the preamble to initiate reception of a message stream. Because of the chirp's distinct pattern, a LoRa gateway can detect signals as low as 20 dB below the noise level. LoRa technology enables -148 dBm sensitivity, enabling robust connectivity with very long range. Furthermore, a LoRa gateway can receive several different transmissions simultaneously, each differing only in sharp batches. As a result, it can support very large number of IoT devices.
LoRa network
LoRa technology's unique modulation method is what makes it so well suited for IoT applications: It can operate successfully over 15 km in rural areas and more than 10 km in urban environments. It can achieve over 10 years of battery life and can operate in networks comprising up to one million nodes. Furthermore, its support for different "chirp" rates, or "spread factors", gives developers the flexibility to manage data rate for range or energy as needed, to optimize network performance (see below).
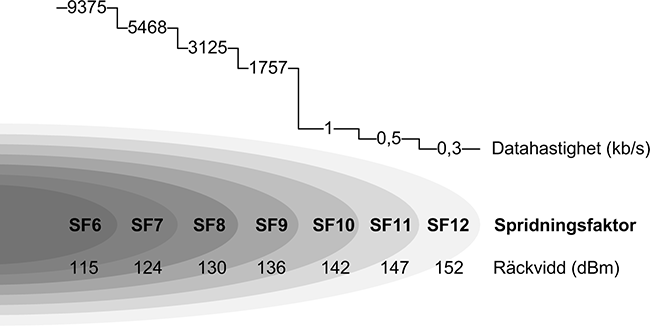
Image from Ambiductor
But LoRa is only the physical layer. In an IoT application, the developer's ability to apply it as a connectivity solution depends on the availability of a network protocol that can build on LoRa. The LoRaWAN standard does just that with its definition of "media access control" (MAC) designed to work with LoRa. Created and maintained by the LoRa Alliance, the LoRaWAN specification is specifically developed for long-range IoT applications and provides access and control via secure, low-power wireless communications.
| Header | Payload |
| Handles the radio communication | The data content in any format |

Image from Scania
LoRaWAN follows a well-known IoT hierarchy of connected things, local controllers and cloud-based servers (see image below). In LoRaWAN terminology, things are connected wirelessly in a star topology to a gateway, and gateways are connected via IP networks to a central network server. The network server decrypts information about which application server the data packet is going to and sends it there.
| Device (sensor/meter) | Gateway | Network server | Application server | MDM-software |
|
All IoT devices send and listen on a programmed schedule to all nearby gateways. |
A multi-channel radio receiver and transmitter for communication. The only thing they see in the telegram is to which network server it should be sent. |
Decrypts a small part of the telegram to be able to control the information further. |
Decrypts the entire telegram and sends back a response to the meter. Can also contain other relevant information for the meter. |
Retrieves all data from an of many APIs or via our FTP server. |
| < AES128 NSK network encryption > | ||||
| < AES128 ASK application encryption > | ||||
| < self built encryption > | ||||
| < virtual cloudbased environment > | ||||
Read more about the topology under What is LoRa?
Communication options
The LoRaWAN MAC protocol is designed to suit IoT applications with different requirements of active communication and sleep mode from a LoRaWAN gateway to an end device. LoRaWAN MAC follows three different classes, all of which support bidirectional communication but differ in downlink availability:
- Class A supports low-power devices such as wireless meters that require minimal communication with the server. An A device can transmit data to a gateway at any time but can only receive within two windows, each occurring at a certain delay after the transmission (see below).

Image from Ambiductor
- Class B is an extended class A with additional reception windows. In addition to the usual two short windows of transmission, a Class B IoT device listens for additional messages at other scheduled windows. The reception windows occur at specific times according to a signal transmitted by a known LoRaWAN gateway. Class B reception scheduling allows applications to contact the IoT device at specific times. Not just under the Class A reception windows.
- Class C supports devices that need near continuous availability of receive windows. A Class C device is constantly listening for messages, except when it is transmitting data or opening the two default receive windows.
Security
LoRaWAN is designed with multiple security features, using a combination of device, session and application encryption keys to encrypt data and to verify device access to the network. For a LoRaWAN application, the things can be programmed from the factory with the authentication information required to connect to a specific LoRaWAN network, which LoRaWAN calls "activation through personalization". LoRaWAN also offers "over-the-air activation", which specifies a procedure of authentication and authorization required for a device to connect to an available LoRaWAN network.
For network control and secure data communication, only IoT devices and the application server contain the encryption key (see below). Encrypted messages are forwarded without being read or manipulated by intermediate gateways and networks, eliminating attacks from hackers.
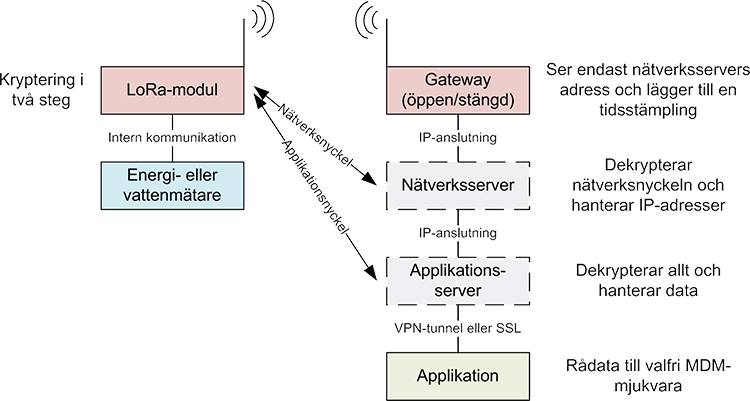
Image from Ambiductor
Encryption keys are only stored in IoT devices and application servers.








